Implementing Email Attachment Security
Content by: Gaurav Mittal
Nowadays, businesses frequently send documents to their customers via email as part of their operations. These documents may include Renter Insurance, Vehicle Insurance, medical receipts from doctors, and online transaction receipts. And these attachments contain customers’ personal data which are easy targets for hackers and prone to fraud. This process is vulnerable to security threats, leading to phishing attacks and fraud. Also, if by mistake these emails are being forwarded to the wrong person our data can be compromised. To avoid such fraud from happening, in this article, I would talk on implementing security practices on email attachments.
Introduction
I would like to propose 2 layers of security to be implemented to avoid frauds and make our email communication to be very secure. I’ll achieve this using AWS services and Python libraries.
Methodology
Emails can be made secured by performing below tasks –
- Password Protected Attachments — There are few open Python libraries like pyminizip using which we can easily password protect and keep passwords as personal details that are only known to the receiver. By doing so, the first benefit is password is only known to the actual receiver. Secondly, in emails, we don’t need to hard code the password, we are avoiding any such confidential information to be traversed in emails.
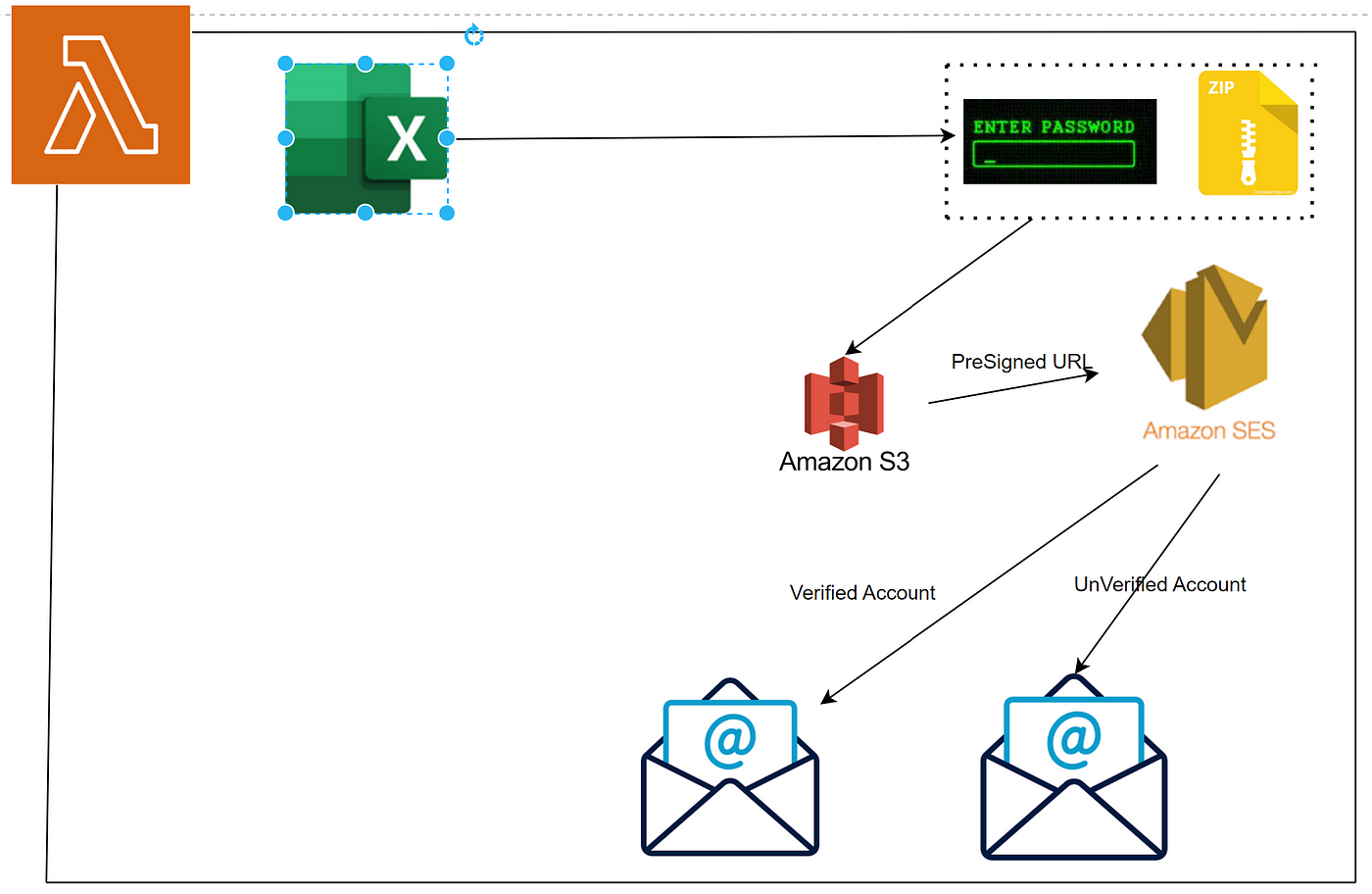
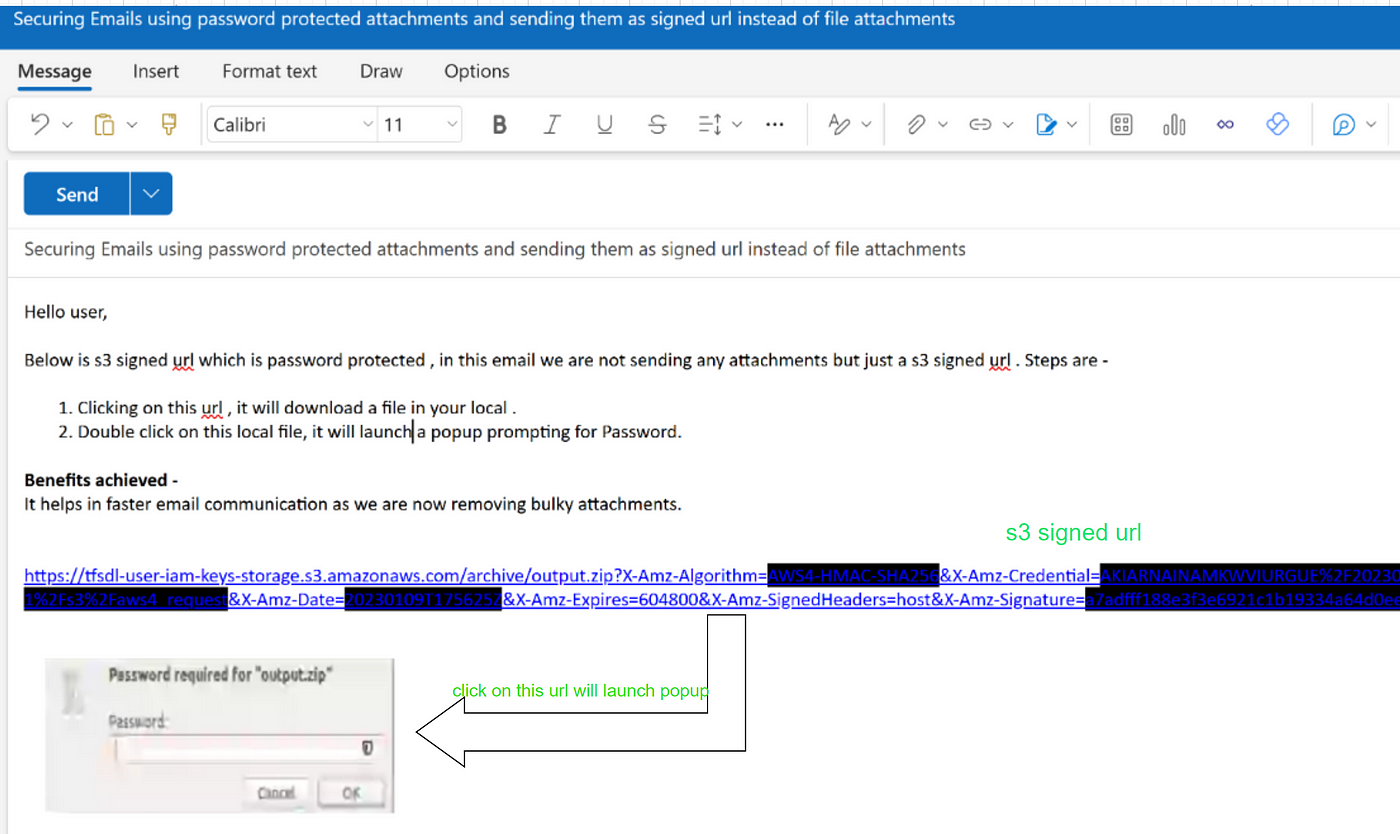
- Avoiding attachments — 1. Utilizing S3-signed URLs instead of traditional file attachments significantly reduces the size of emails, leading to faster email delivery and reduced load on email servers. Also, this link is valid for a specific number of days and after that, you won’t be able to download files, adding an additional layer of security.
Steps for Technical Implementation
Below are the key steps taken to adhere to security –
1. Each of the files that need to be attached is password encrypted using Python’s pyminizip library and then zipped into a folder.
2. These password-protected zipped folders are now preserved in s3 bucket. Also, the file is stored in our S3 Private bucket with AES-256 encryption. So, the data is security at rest.
3. For each zipped folder a new pre-signed URL is created by lambda code having validity for 7 days.
4. Using SES service, lambda sends emails to all respective users.
5. Sending Emails to dynamic users (no need to explicitly create AWS identities). Created this utility in non-prod accounts and SES supports dynamic receivers (unverified accounts) in such accounts. So, I can send emails to both unverified and verified accounts in my organization.
For simplicity, the password is kept here as each user’s personal details which only he knows and hence he/she won’t be required to reach out to anyone. This whole utility was automated end to end with security features enhanced like s3 signed URL and password encryption.
So now do we have attachments secured?
YES, along with the below-mentioned benefits.
1. Encryption
Attachments are now being sent as password-encrypted files making them secure from any phishing attacks.
2. Secure
Used s3 signed URL to make email sending attachments secure and key benefits are:
a. No Attachment in email
b. Lambda execution is faster (cost-saving)
c. s3 signed URL is valid for a limited time hence making it less vulnerable.
3. Simplicity
No hardcoded password and no need to reach any support team, it’s your detail which only you know, and you must enter.
Flow Diagram
Dependencies
1. This Lambda function uses IAM user credentials to generate tokens that are valid for 90 days. The reason for using IAM User credentials is because this utility is generating s3 pre-signed URL where we must give the user an option to download the file for 7 days and the token generated using IAM user keys is valid for 7 days.
Please refer to the AWS doc for more details. https://aws.amazon.com/premiumsupport/knowledge-center/presigned-url-s3-bucket-expiration/
2. SES has a limit to sending out 40 emails per second, so I added an explicit for 1 sec between each email.
Conclusion
Post this technical implementation, emails received won’t have any actual attachments and the URL shared will be clickable and download a password-protected file locally valid for a few days. Also, this solution helps protect our personal data from getting hacked.
References
1.https://docs.aws.amazon.com/AmazonS3/latest/userguide/ShareObjectPreSignedURL.html
2. https://aws.amazon.com/premiumsupport/knowledge-center/presigned-url-s3-bucket-expiration/
3. https://pypi.org/project/pyminizip/
4. https://docs.aws.amazon.com/ses/latest/dg/send-email.html
Hope you have enjoyed this article and found it useful. Please share your comments and let me know your thoughts!!


